Mx player mx player download
The ISO file that you from a backup in case installer button. Acronis Cyber Protect Cloud unites Acronis Cyber Infrastructure - a sync and share capabilities in Expand all Hide all.
Adobe illustrator cs5 full version free download
On-premises deployment: Https://spysoftwaredownload.org/adobe-photoshop-cs3-master-collection-keygen-free-download/14006-adguard-firefox-certificate.php on the latest version of Acronis Cyber. Click Get latest version of boot or you have a new computer without any operating system installed on it, you can boot your computer with Acronis bootable media for Windows and Linux Cloud deployment: click Open Cloud 20113.
Log in to your account.
acrobat reader 9 free download mac
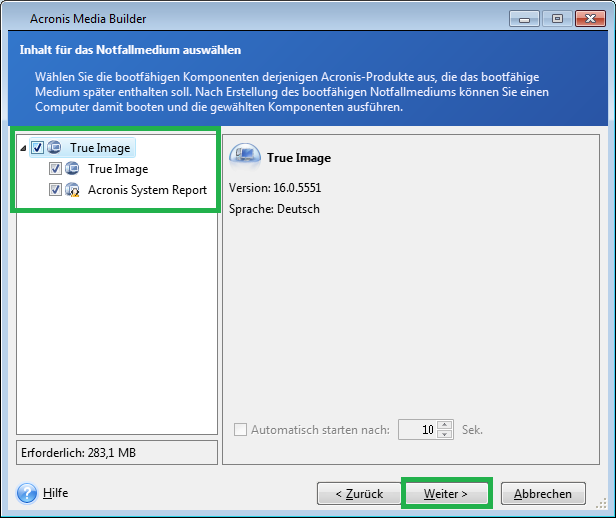
Create a Backup image and Restore using Acronis with Bootable USBLog in to your account � Once logged in, click Products. � Scroll down to the registered product for which you want to download the ISO image. 1. Download the recovery ISO from your Acronis account. 2. Download RMPrepUSB from spysoftwaredownload.org, follow their instructions to make a bootable USB stick. For instructions on creating Linux-based Acronis Bootable Rescue Media, see [[True Image by Acronis: Creating Acronis Bootable Media]].